Amazon is not the first company that comes to mind when the words “privacy” and “honesty” are part of a conversation. Far from it, actually. Remember, this is the same company with such shit data protection policies that its employees could even peek into the cart of a celebrity who bought dildos. The cutesy Alexa speaker recorded people having sex while employees allegedly enjoyed those pervy carnal clips.
Scams are just another delightful feature of Amazon’s expansive e-commerce empire. Unfortunately. Amazon seems quite content to leave things as they are. And good luck getting them to issue refunds or send replacements—it’s practically a lost cause.
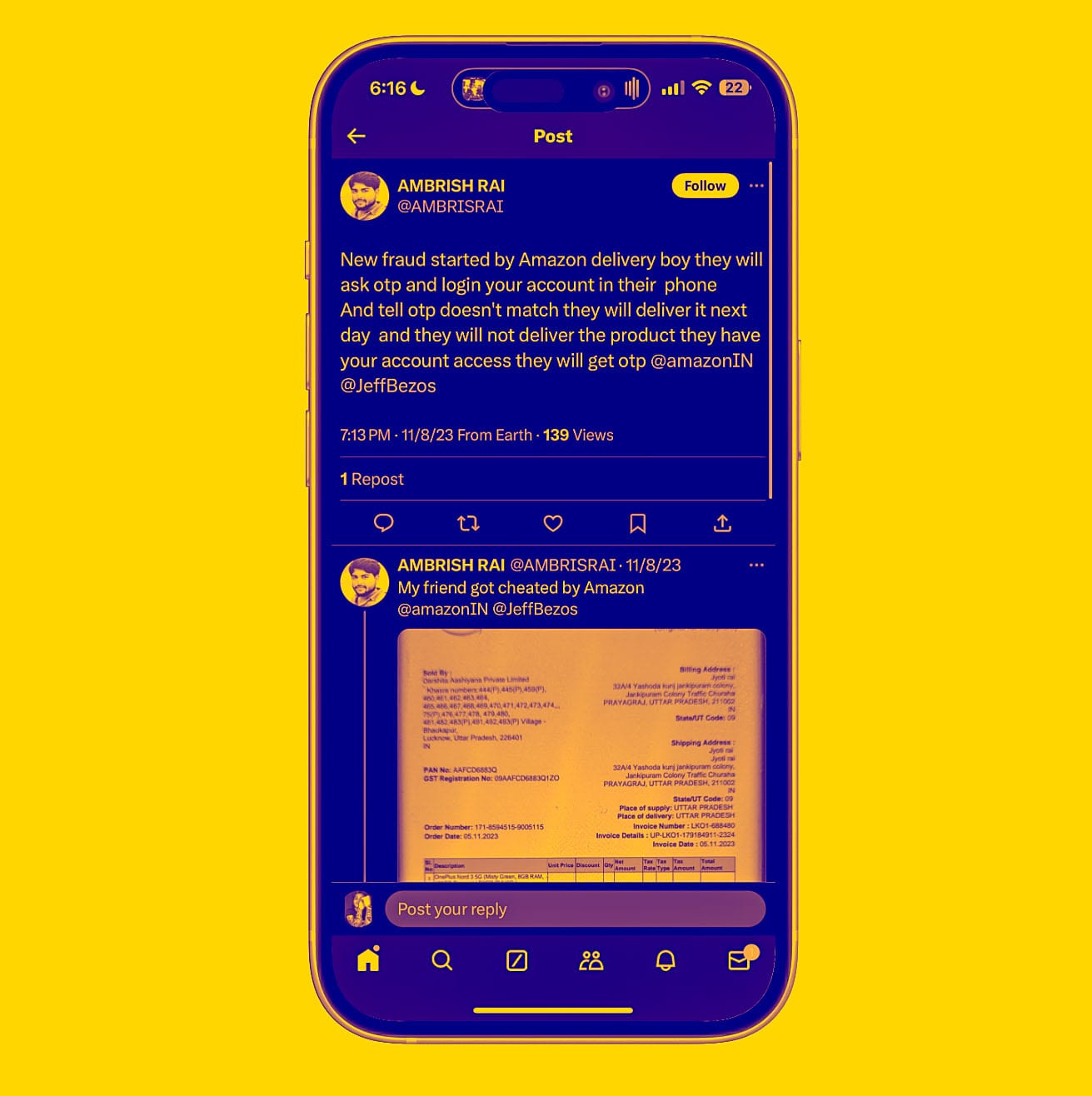
Ah, look, another flavor of Amazon delivery scam.
The latest in a line of brazen scams is a seemingly legitimate Amazon logistics executive calling you requesting an OTP, which they promptly abuse to take over an unsuspecting person’s account.
Oh, this is not just based on the many, many testimonies that you can find on X, the god-awful platform formerly known as Twitter. This happened to me a few days ago, and had I not paid attention to the language of the SMS message sent by the scammers, my Amazon account would have been a goner.
Two targets of the OTP attack told Athenil they had no idea about the right emergency steps to protect their account, except blocking the charlatan's calls and messages. At least three of the targets recall getting panicked about potential financial loss and immediately changed their account password.
Here’s how this scam unfolds:




Now, there are a lot of red flags, but for an average person who is not well-versed in the sophisticated and eerily realistic world of online scams, it’s easy to take the bait. But even before the trick is put into action, there are a few questions that Amazon must answer:
- How did my phone number land in the hands of scammers?
- How do these fraudsters know the details about my order, specifically what the item was and when it was delivered?
- How are scammers able to trigger the account sign-in process without knowing the password to my account?
- Amazon allows logins using either your email or phone number, after which you enter your password. Only when you’ve enabled two-factor authentication, do you get a code to verify that it is you (the real owner) trying to access the account.
The only other scenario where an OTP is triggered is when you (or another person) are trying to change the login credentials. So, how did the scammers get as far as triggering an OTP on the registered phone number for a target account?
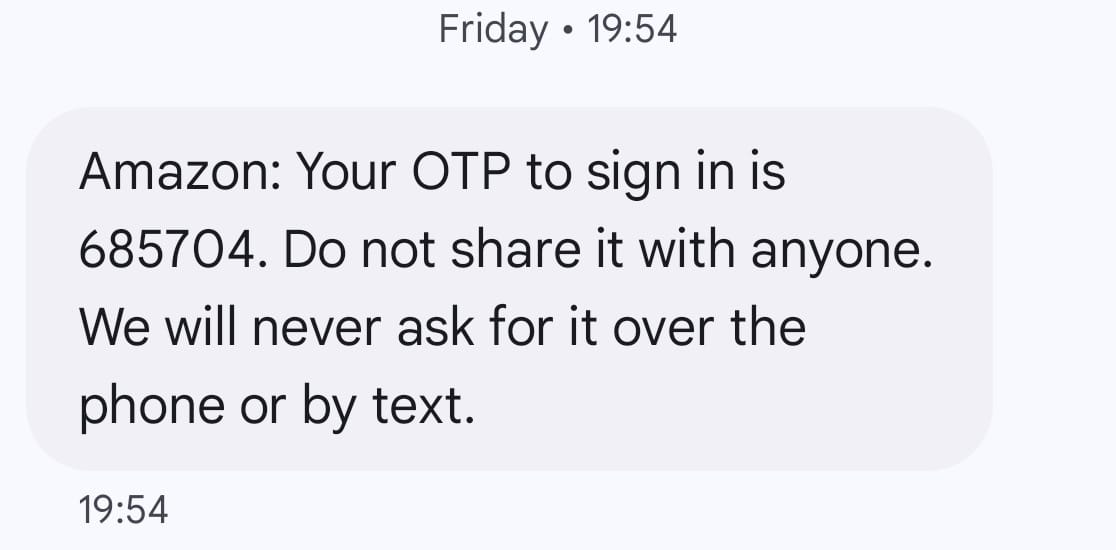
Now, keep in mind that there’s still a healthy bunch of online shoppers out there who haven’t enabled two-factor authentication. But what’s even more dangerous is folks who get a bajillion SMS codes on their registered phone number, but don’t bother to read (or are able to make sense of) the message’s contents.
Below is a sample of the OTP message that I received on my phone after the scammer tried to log in to my Amazon account.
This is the message with an OTP that you get when an order is delivered and you need to verify with the delivery agent that you are the rightful recipient of the package.
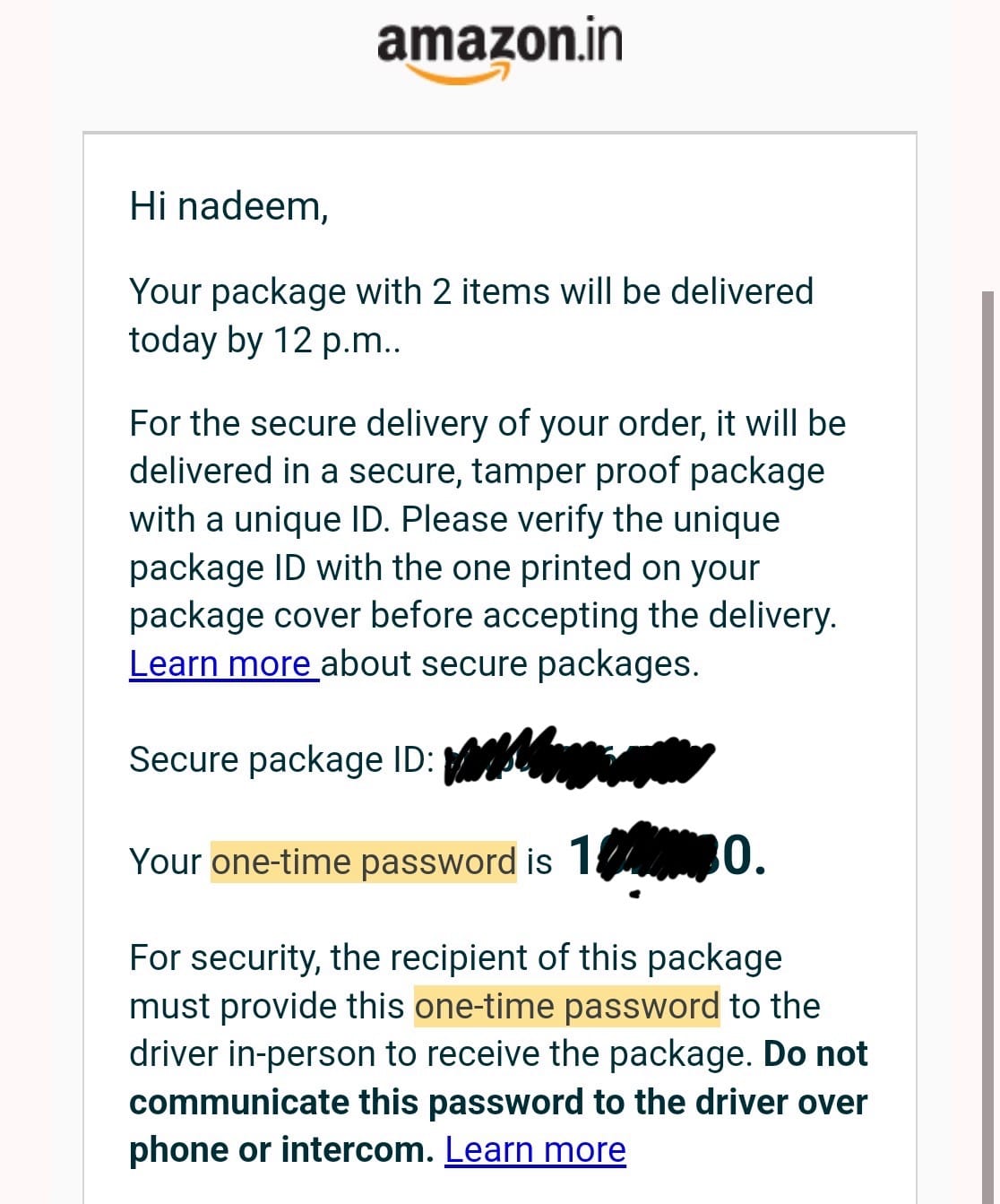
Now, it seems the scam has been going on for a while. And there are a few things that absolutely don’t make any sense, at all. Let’s assume, for once, that your mobile number has already popped up in a countless number of data dumps selling for peanuts in some corner of the web.
But how does a scammer know exactly what I ordered and the date it was delivered? That leaves us with the following possible conclusions:
- Amazon’s delivery partners are colluding with fraudsters and handing over customer shopping data to them.
- Amazon’s employees have gone rogue and are abusing their access to customer data and using shady numbers to fish them for OTPs via phone calls and messages.
- Amazon’s logistics partners or reseller partners have cracked the code for abusing systemic flaws that let them exploit gullible online shoppers without any fear of repercussions.
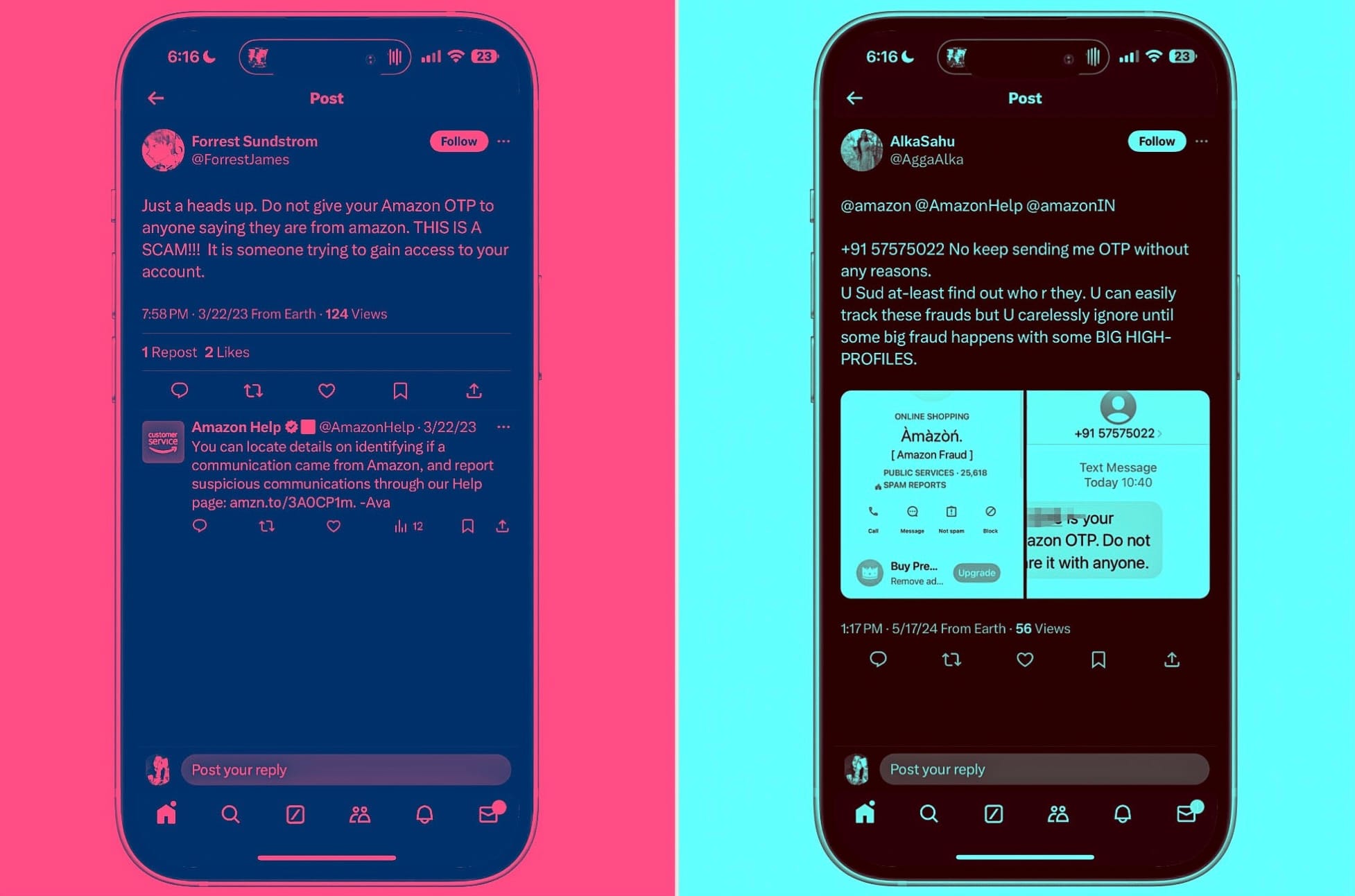
Now, a quick search for the keyword “Amazon OTP fraud” on social media pulls a heck ton of users complaining of related OTP scams. In some cases, the delivery agent calls the customer, asks for the OTP to complete the package hand-over (as per protocol), and checks it off as “delivered” in the system without actually delivering the product.
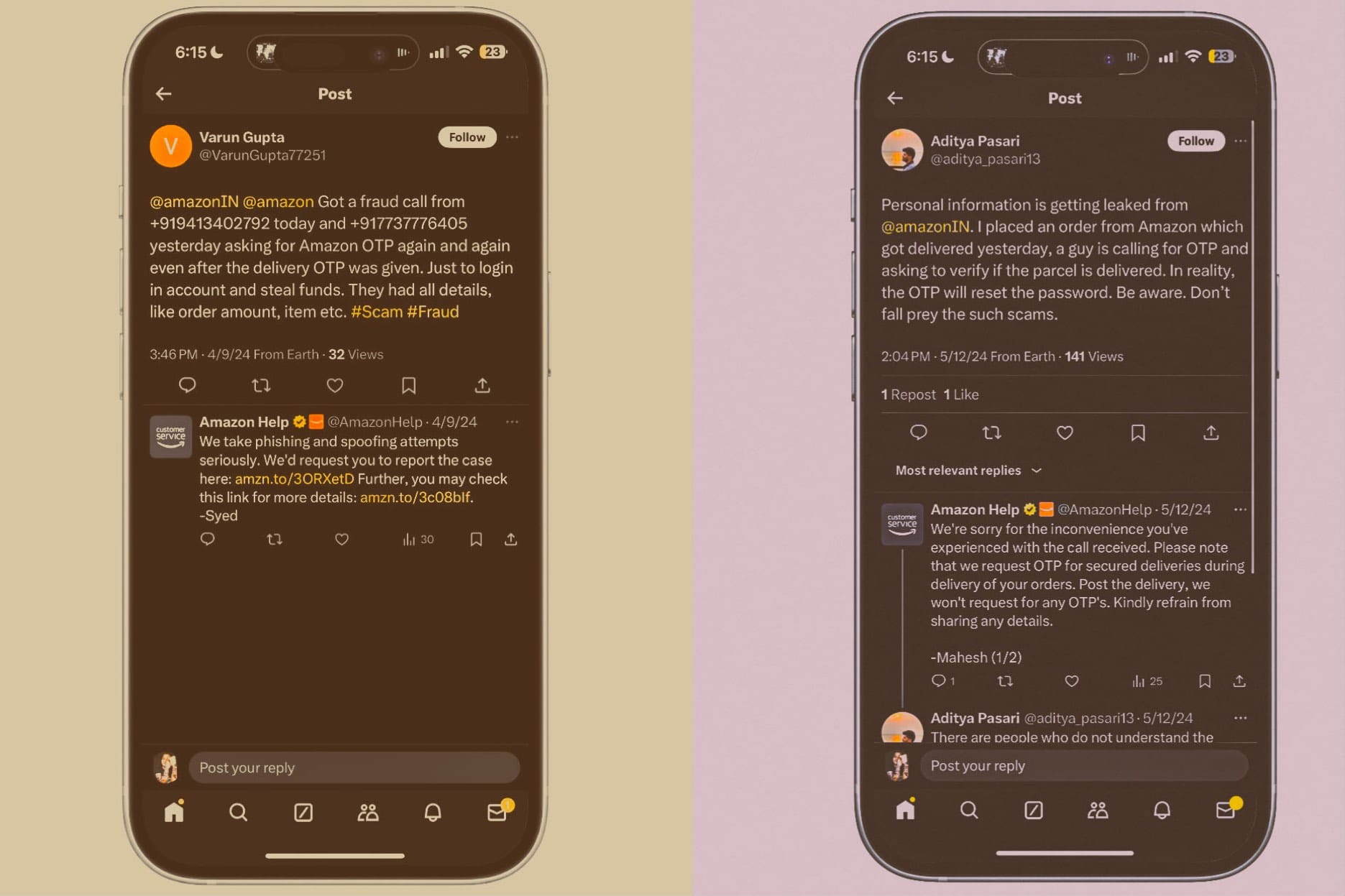
There’s another related variation of this scam. Apparently, if you order multiple items, and more than one item is scheduled to be delivered on the same day (or in one go), Amazon assigns a single OTP for the entire consignment. With that knowledge, a delivery agent reaches the customer’s doorstep, drops only one product, but checks off multiple products as delivered in the system.
When the flabbergasted customer realizes that they have received only one item but the status has been marked as delivered in their Amazon shopping dashboard, they reach out to Amazon support for help. But in a lot of cases, they just end up paying for products that they never received in the first place, and don't end up getting any help from Amazon.
In my case, when I asked my delivery agent if they shared my order details with any other individual, they didn't answer citing it was an internal matter. As for the fake delivery executives, well, they turned abusive the moment I expressed knowledge of their scam.
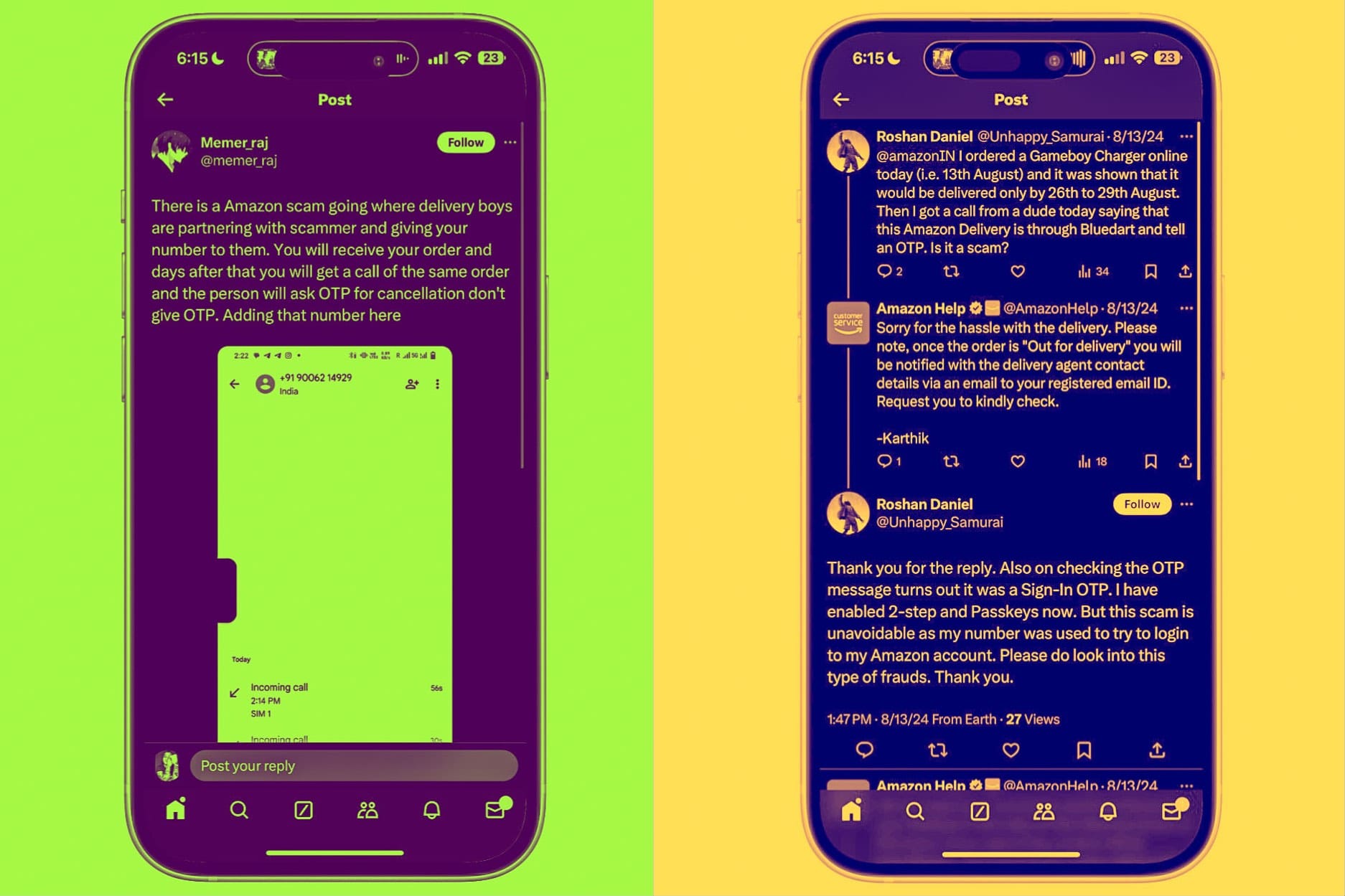
In some cases, the aggrieved customer has even posted CCTV camera footage where only one product reached their doorsteps, but the delivery agent checked off multiple products as delivered.
And yet, despite sharing the evidence with Amazon support, no help was provided to the victim. Now, let’s get back to the OTP part. There are a lot of ways it can be abused, and there’s evidence to justify that based on public complaints by hapless Amazon customers.
How do scammers know my order history, Amazon?
First, the OTP comes in as a sign-in prompt, which means it’s an account takeover request. The most benign thing that a bad actor can do at this stage is that they can check off products as delivered and keep the package for themselves. It’s pretty easy to do so.
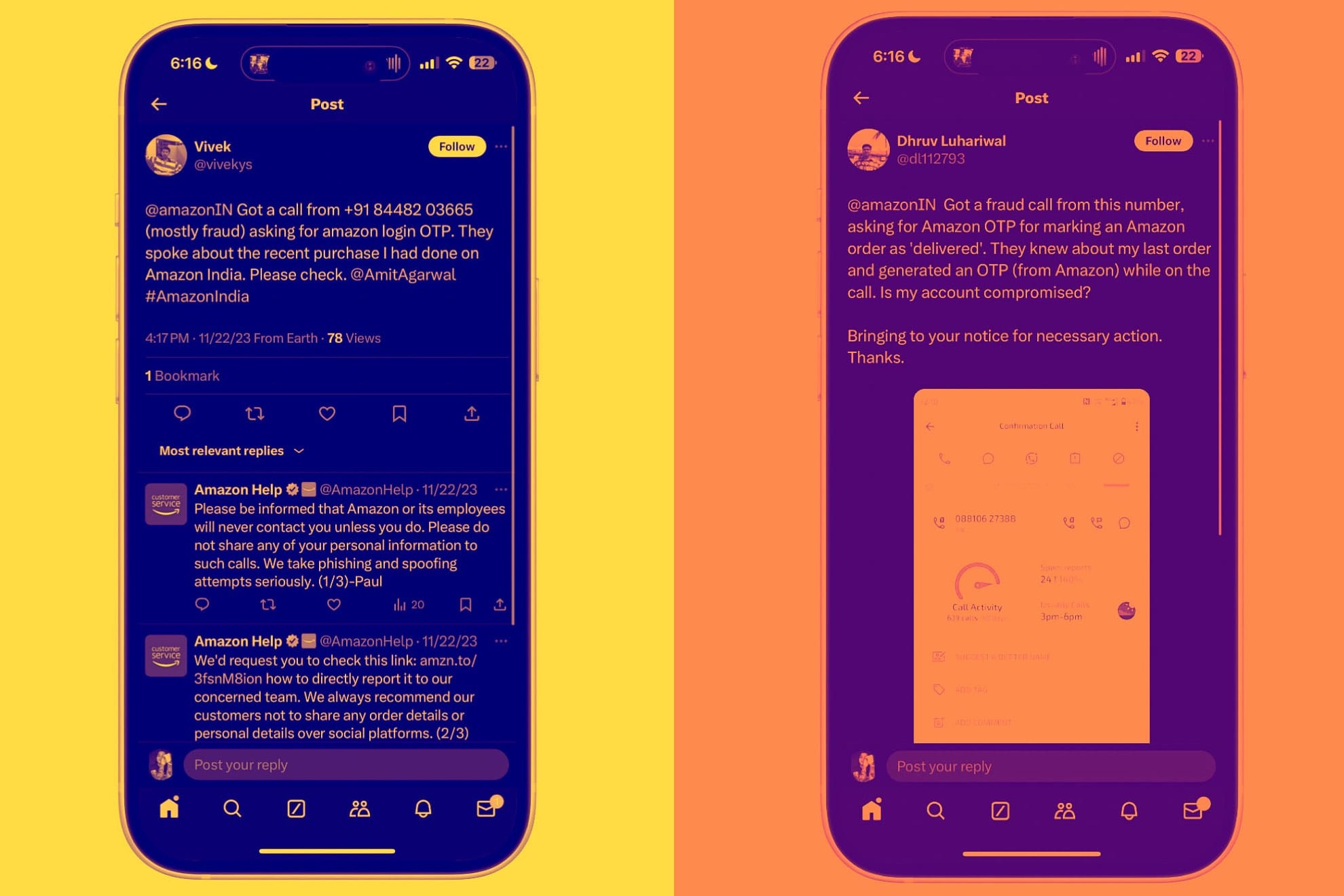
Once a bad actor has access to your account, they will send an OTP to initiate the delivery of a product. Since they have access to the Amazon account of the victim, they receive the OTP, enter it into the logistics system, and mark the product as delivered.
Looking at the more sinister scenario, the scammer can simply use the OTP phishing trick to reset the account details, which not only includes the password, but also the linked account and phone number. In a nutshell, the victim loses access to their Amazon account fully, without a way to recover it.
Similar trickery has also been used to hoodwink customers with an Amazon Pay account. There is no dearth of Amazon customers who are flummoxed at the availability of sensitive information in the hands of customers, which essentially creates a cakewalk-like situation for fraudsters to trick online shoppers.
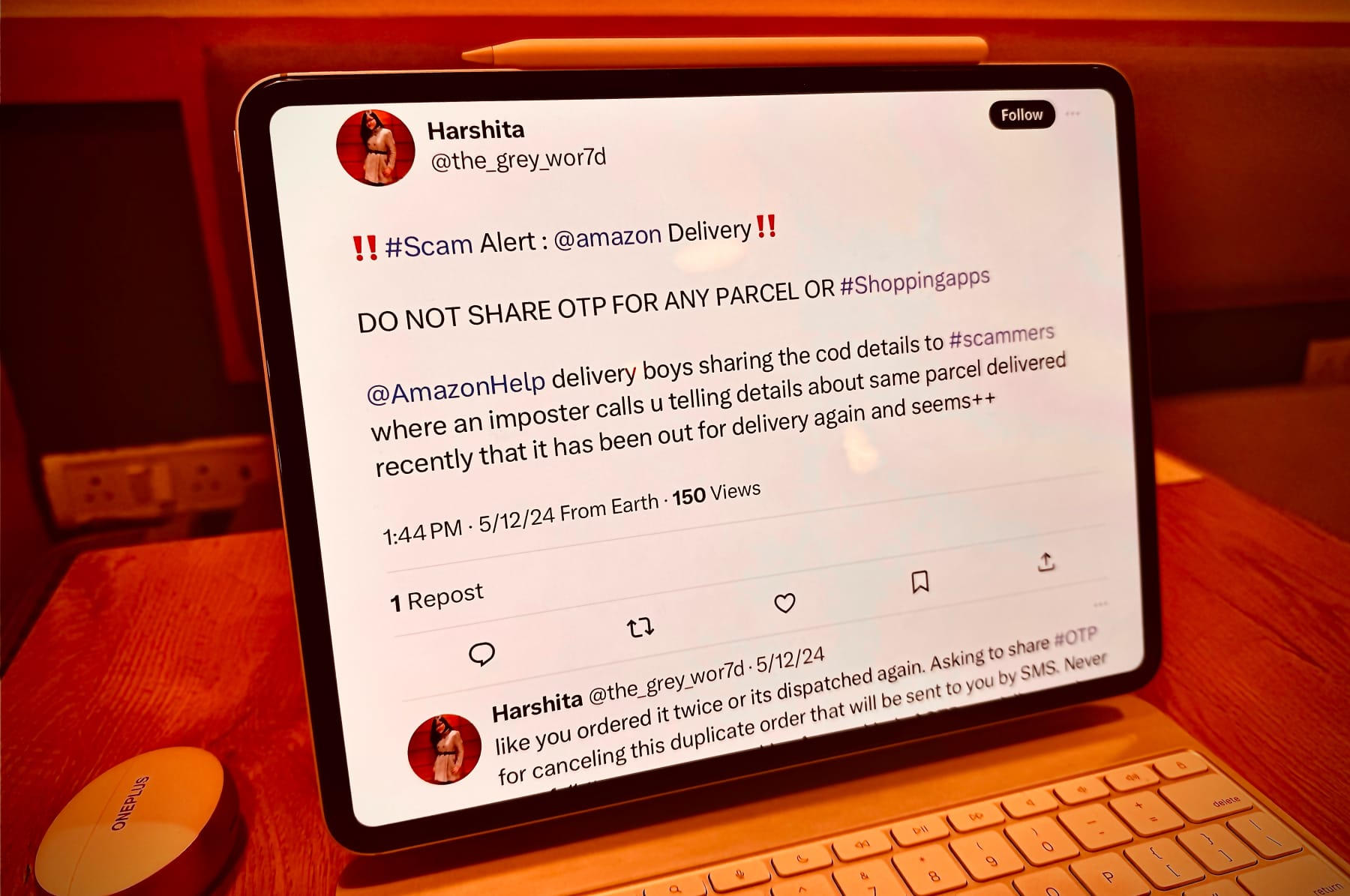
A related, but fairly well-documented modus operandi, is scammers calling customers about cancellation of an order they never placed. Feigning urgency about return or loss of money, the swindler tells the customer that they need to share an OTP sent on their registered phone number to secure the order.
There are virtually unprecedented ways in which an online finagler can scam an unsuspecting Amazon customer. And the worst part is that — combined with the poor digital literacy situation — the victims usually have to run from pillar to post seeking relief, which often doesn’t ever arrive.
On an official support page, Amazon lists “do not share any OTP” under Customer Obligations. It’s nothing short of cruel when Amazon itself has created a whole business that relies on an OTP as the trust token for products to exchange hands and keep account security intact.
To each their own... peril!
Until Amazon comes up with a more resilient system and plugs the loopholes in its logistics system that facilitate such scams in the first place, scammers will keep finding ways to exploit shoppers. It’s an endless chase, and without a deep systemic overhaul targeted at security measures, Amazon customers will continue to live at the mercy of cybercriminals.
For now, the best suggestion that I can give is to read the contents of an OTP very carefully, only give an OTP in person to an Amazon agent (not over a phone call or text), and always verify the contents of the package before the delivery agent leaves your doorsteps.
And for the love of the Lord Almighty, enable two-factor security. That way, every sign-in attempt will at least have to pass through your inbox with a security code. At the end of the day, none of it is an infallible solution, but the best an average online shopper can do.
As for Amazon, well, get your shit together!

